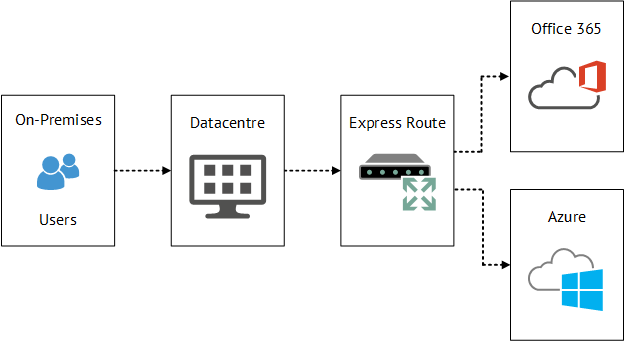
When I think about Media Services, automatically the complexity of delivering content springs to mind. How do I get the footage from my location to a website securely? How do I then deliver the footage so that it can be consumed? How do I make the footage available offline? How do I make sure the footage is only available for a set period of time?
Well if you are famous then you probably have a team of people who worry about this for you. For us common folk, we have to rely upon a third party service. This is where Azure Media Services can help.
What Is Azure Media Services
According to Microsoft, Azure Media Services enables developers to create a scalable media management and delivery platform. What this really means is it allows you to provide live streaming or on demand access to audio and/or video content in a secure manner.
What Makes Up Azure Media Services?
The first thing you need is an ‘asset’. Think of an ‘asset’ as a container that holds all of the files that make up your movie. The ‘asset’ is then mapped to a blob container. Each ‘asset’ must contain a unique version of the media content. For example if you have Star Wars IV and Star Wars IV Remastered these need to be in separate ‘assets’.
Next we have an ‘asset file’ which is a digital media file stored on the blob container which is associated with you ‘asset’. Each ‘asset’ can be encrypted using one of the following options:
| Option | Encryption |
| None | No Encryption |
| Storage Encrypted | Encrypted locally using AES 256. Stored in Azure on encrypted storage |
| Common Encryption Protected | Encrypt content with Common Encryption or PlayReady DRM |
| Envelope Encryption Protected | Encrypt HTTP live streaming (HLS) with Advanced Encryption Standard (AES) |
An asset policy is then applied to the ‘asset’ to determine permissions to the resources and the duration of the access, for example you might want to allow everyone to view a live stream of an event. But then you might want people to register to download the event for offline viewing.
It’s important to note that the blob storage container is the boundary for access to the ‘asset’. To access the media content, locators are used which are essentially entry points. These can be either on demand for streaming or SAS (shared access signature) URL based.
- Bandwidth is purchased in 200Mbps increments
- Default of two streaming endpoints per Media Service account
Before media content is stored in Azure, you might want to encode it. This process is known as a ‘job’, each ‘job’ contains a number of tasks which are performed. For example, you might want to to encode a video so that it is compatible with common web players and mobile devices.
Last of all we have channels, the best way to think of these are like channels on TV. Each Media Service account comes with five channels. Within each channel is a program. Think of these are a timed even on a channel. You can have three concurrent programs running on your five channels at any given point in time.
Probably a bit easier to explain the above in a diagram, so here it is.