When you shift your focus from on-premises architecture to cloud based services, you notice that the velocity of updates and new features is relentless. To give you an idea, over the last 12 months Microsoft have released over 500 updates on the Azure platform, some of these are feature enhancements, betas, public previews and new services.
When you shift your focus from on-premises architecture to cloud based services, you notice that the velocity of updates and new features is relentless. To give you an idea, over the last 12 months Microsoft have released over 500 updates on the Azure platform, some of these are feature enhancements, betas, public previews and new services.
Microsoft Azure is a moving target keeping up to date with enhancements is a full time job!
With this in mind, I thought I would share with you , the feature enhancements over the past few months that have had the biggest impact to the customers I work with.
Azure DevTest Labs – Ability to set an expiry date on virtual machines
We all know that development environments should only be up and running for a short amount of time to facilitate an application enhancement or initiative. However in reality the virtual machines which were only meant to be temporary, end up being on all the time with everyone afraid to power them off ‘just in case something bad happens’.
With Azure DevTest Labs we can now harness the inbuilt functionality to set expiry dates to virtual machines. Sounds trivial but what a great feature addition to manage the compute resources around a VM lifecycle.
Read more here.
Azure Automation – Start/Stop VMs (Preview)
We are used to having our on-premises VMs running 24×7. Because we have already invested in the compute and storage infrastructure so what is the real use case of shutting them down? Instead we sweat our assets for the three to five year hardware lifecycle and rinse and repeat.`
Taking the same architecture principles to a cloud based platform increases costs. Why not get smart and reduce your consumption costs by targeting applications to when users access them? If HR only work Mon-Fri 9-5 and access Sage during this time frame, then why not power on the VM at 8am and shut it down at 6pm? Reducing your Azure consumption costs by 58% over a 12 month period.
Read more here.
Azure Managed Disks
When running virtual machines in Azure it’s not just a simple case of creating a storage account, factors such as the number of virtual machines per storage account with their IOPS requirements as well as the impact that backups have need to be taken into consideration.
These manual considerations can be negated to a point using Azure Managed Disks in which Azure handles the Storage Account in the back end reducing your management overhead.
With the general availability release of Azure Managed Disks integrate with Azure Backup and also Disk Encryption.
Read more here.
Automated Backup for SQL Server 2014 and 2016 Virtual Machines
It can be common for enterprises to backup SQL Server databases outside of the general backup schedule applied to other applications. With the release of Automated Backup for SQL Server 2014 and 2016 Virtual Machines this can be automated for you with the creation of the VM.
With a daily backup and a retention period of 30 days, this adds another layer of protection to your backup routine.
Read more here and here.
Azure Backup Instant File Recovery (Preview)
Azure Backup has always done a job, but backing up a VM level has had its disadvantages namely having to restore an entire VM to an alternate location to get back a single file or folder.
Azure Backup Instant File Recovery creates a writable mount point attached to the VM you want to restore data too using an iSCSI target. This simplifies the process and reduces management overhead.
Read more here.
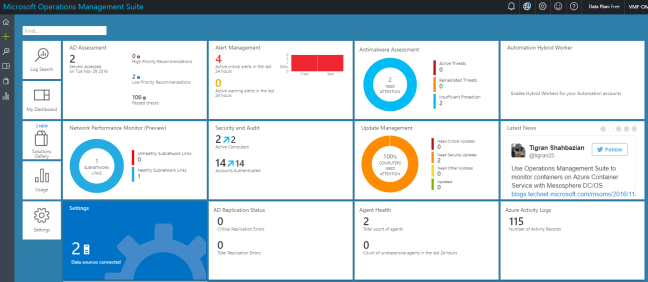
Azure Security Center Enhancements (Preview)
The Azure Cyber Security team have announced a number of the new enhancements which are in preview. The most poignant ones are:
- Application White Listing – Allow only the authorised executables to run within the virtual machine, with Azure Security Center discovering and recommending white listing policies
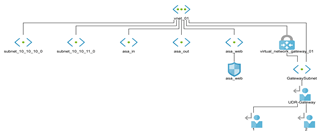
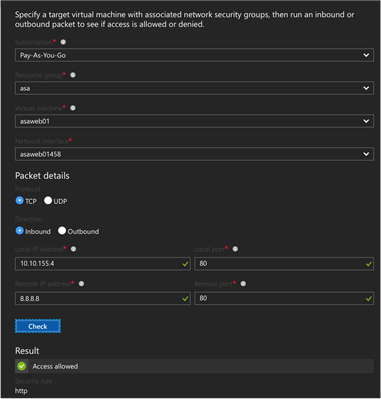
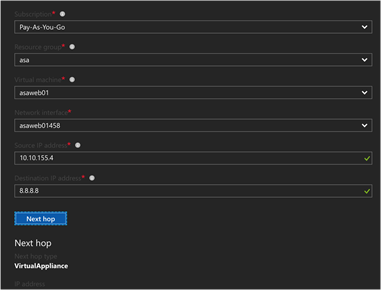
- Just in Time Network Access to VM’s – Reduce your attack surface by only allowing access to common ports when required
By simply deploying the above two changes, I can see a benefit for most organisations to enhance their security footprint.
Read more here.