With the increased uptake of Azure across both public and private businesses, we are starting to see identity gaps across business divisions creating pockets of isolation.
In the diagram below we have a single Enterprise Enrollment which has two Azure Accounts, one for Online Services and the another for Retail Stores. Underneath these we then have two Azure Subscriptions, one for Development and the other for Production.

You might wonder what the issue is? Well in this scenario we have a single on-premises corporate directory that services ‘Online Services’ and ‘Retail Stores.
- ‘Online Services’ have setup their on-premises corporate directory to integrate with Azure AD, so that their starters and leavers process is controlled using their existing directory service.
- Whereas ‘Retail Stores’ have no integration to the on-premises corporate directory and are using the default on.microsoft.com accounts
Both business divisions have rolled out Production & Development services, but we need to close the security gap to ensure that both divisions are using the corporate directory as part of their identity model.
To achieve this we have two choices available to us, Transfer Directory or Subscription.
A subscription can only be associated to a single directory
The next part of this blog post has been written by my colleague Graham Lindsay, Lead Architect and one of our identity experts.
Transfer Directory
This will not change the Account Admin or the billing, it purely modifies which directory the subscription is linked and can be completed using portal.azure.com.
Create Guest B2B account in the receiving directory using the email address of the Service Admin of the subscription to be switched . This can be a standard non admin user.

From the service admin account accept the B2B invite.

Once the service admin account has accepted the B2B invite it will now be able to view the receiving directory within the directory switcher.
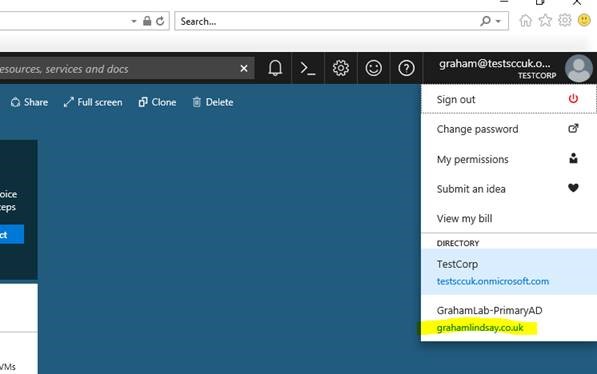
Staying within the subscription hosting directory (TestCorp) locate the subscription to be transferred and choose change directory.

From the drop choose the receiving directory being (GrahamLab).

Once the change has occurred, the subscription will no longer be accessible in the in the TestCorp Directory.

Using the directory switcher specify the receiving directory.
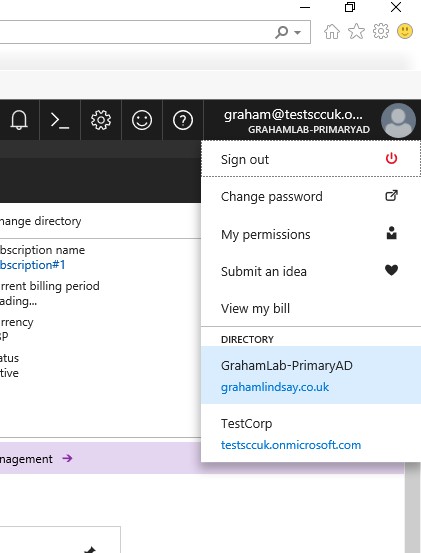
Open Subscriptions and you will now see that the subscription has now moved. You can now rebuild the RBAC on the subscription.

Transfer Subscription
First of all it’s worth noting that only the following Subscriptions can be transferred.
- Enterprise Agreement (EA) MS-AZR-0017P
- Microsoft Partner Network MS-AZR-0025P
- MSDN Platforms MS-AZR-0062P
- Pay-As-You-Go MS-AZR-0003P
- Pay-As-You-Go Dev/Test MS-AZR-0023P
- Visual Studio Enterprise MS-AZR-0063P
- Visual Studio Enterprise: BizSpark MS-AZR-0064P
- Visual Studio Professional MS-AZR-0059P
- Visual Studio Test Professional MS-AZR-0060P
Subscriptions can only be transferred to someone in the same country
When transferring the subscription this changes the entire subscription including billing.
- For Enterprise Agreements this is done in the EA portal
- For Non-Enterprise Agreements this is done in the billing portal
Within the billing portal locate the subscription to be transferred and choose transfer subscription.
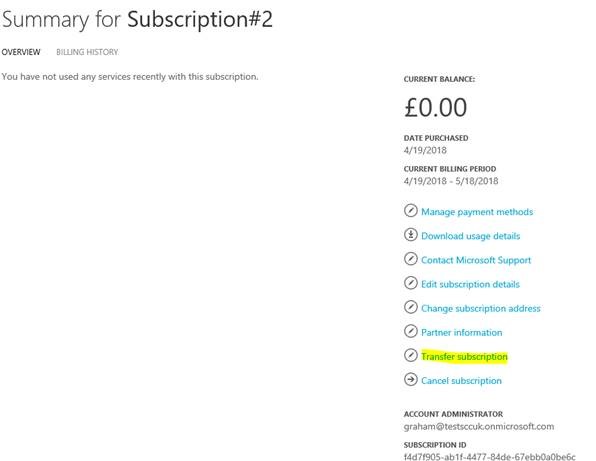
From here you can just change just the Account Admin or you can change the Account Admin and where the subscription is linked to. To transfer the whole thing and change the service administrator as well untick the retain this subscription with my AzureAD.

Enter the name of the account who will be taking over the subscription (I chose to switch the AzureAD directory too)

The following screen is shown saying that the transferred has started.

The receiving party will also receive an email will a link to initiate the transfer. Clicking this link the following is shown with the following screens shown.

The subscription is now shown as transferred in the sending portal as transferred.

The subscription is now showing as active in the receiving portal.
As you can see the service admin is updated too.




 It’s been a few months since I wrote my last ‘Azure Announcements’ blog post so thought it would be worth sharing a number of features which I have my eye on.
It’s been a few months since I wrote my last ‘Azure Announcements’ blog post so thought it would be worth sharing a number of features which I have my eye on.









 As part of transitioning my lab to Hyper-V I’m using a HPE StoreVirtual VSA to provide shared storage to the Hyper-V Hosts.
As part of transitioning my lab to Hyper-V I’m using a HPE StoreVirtual VSA to provide shared storage to the Hyper-V Hosts.

